Strict Act-as Mode
When Strict Act-As Mode is enabled, workflows are not executed directly by the Dataform default service account. Instead, Dataform default service account acts as a custom service account that holds a specific and limited set of permissions. This pattern, known as service account impersonation, is a standard security practice in cloud identity and access management. While widely used, it can be confusing if you are not familiar with it. The Dataform default service account is responsible for orchestration within Dataform, while the custom service account is responsible for execution against BigQuery.
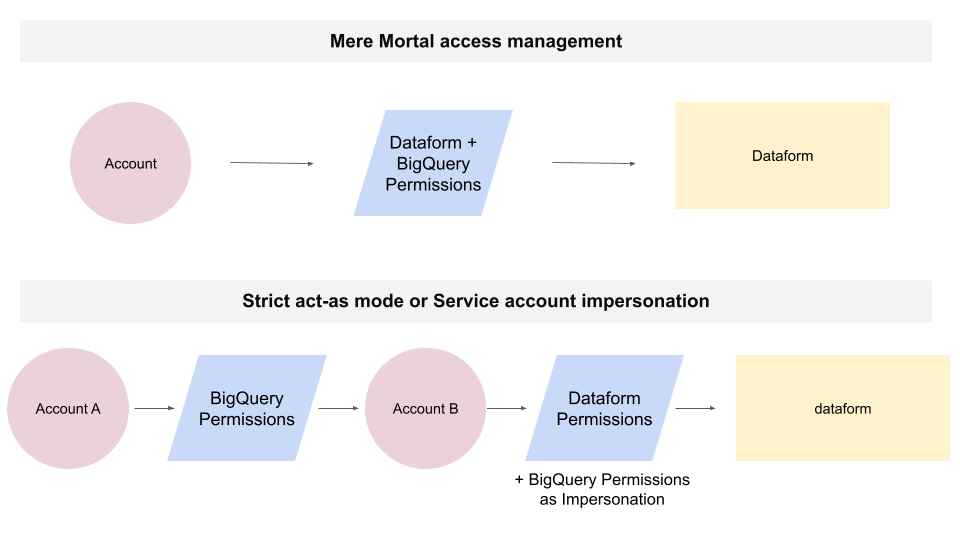
Service account impersonation allows the permissions required to perform a task to be separated from the identity that initiates the task. This separation helps enforce several basics security and access management principles:
-
Principle of Least Privilege (PoLP)
A service account should only have the minimum permissions required to perform its specific function. Granting excessive permissions increases the blast radius if that account is compromised. -
Isolation and Scoping
Service accounts should be scoped to a single responsibility or system boundary, rather than shared across multiple services or workloads. -
Auditability and Accountability
Every action performed in the system should be traceable to the service that initiated it. With impersonation, orchestration actions are clearly attributed to the control plane, while data access actions are attributed to the execution account. -
Credential Management
Service account impersonation relies on short-lived access tokens, issued only when needed and automatically rotated. This eliminates the need for long-lived static keys and significantly reduces credential leakage risk.
Strict Act-As Mode in Dataform encourage to applies these principles as follows:
-
Principle of Least Privilege
The Dataform service agent only holds permissions required for orchestration tasks such as managing workflows, reading repository metadata, scheduling executions, and requesting impersonation. It does not have direct access to BigQuery data. -
Isolation and Scoping
The default service account is dedicated to Dataform orchestration, while the custom service account is scoped exclusively to BigQuery access. If the default service account is compromised, no access to BigQuery is possible. If the custom service account is compromised, no Dataform orchestration or execution can be triggered. -
Auditability and Accountability
Because execution occurs via impersonation, it is always clear which service orchestrated the run and which service account accessed the data. -
Credential Management
The execution service account uses short-lived credentials that are never stored or long-lived, and BigQuery access exists only for the duration of the workflow execution.
In practice, this results in the following role distribution:
-
Custom Service Account - Execution
-
BigQuery Data Editor
Allows creating, updating, and deleting tables and views in BigQuery datasets.
Used to materialize tables, overwrite partitions, and manage transformation outputs. -
BigQuery Data Viewer
Grants read-only access to tables and views.
Required to read source data during query execution. -
BigQuery Job User
Permits running BigQuery jobs (queries, loads, extracts).
Without this role, the account could not execute SQL even if it had dataset access.
-
-
Default Service Account - Orchestration
-
Dataform Service Agent
Allows Dataform to manage repositories, schedules, compilations, and workflow executions.
This is required for Dataform itself to function. -
Secret Manager Secret Accessor
Enables reading secrets (e.g., credentials, tokens) needed at runtime.
The account can access secrets but cannot modify or create them. -
Service Account Token Creator
Allows generating short-lived access tokens to impersonate the execution service account.
This is the key permission that enables secure service account impersonation.
-
This is the default configuration set by GA4Dataform installer.
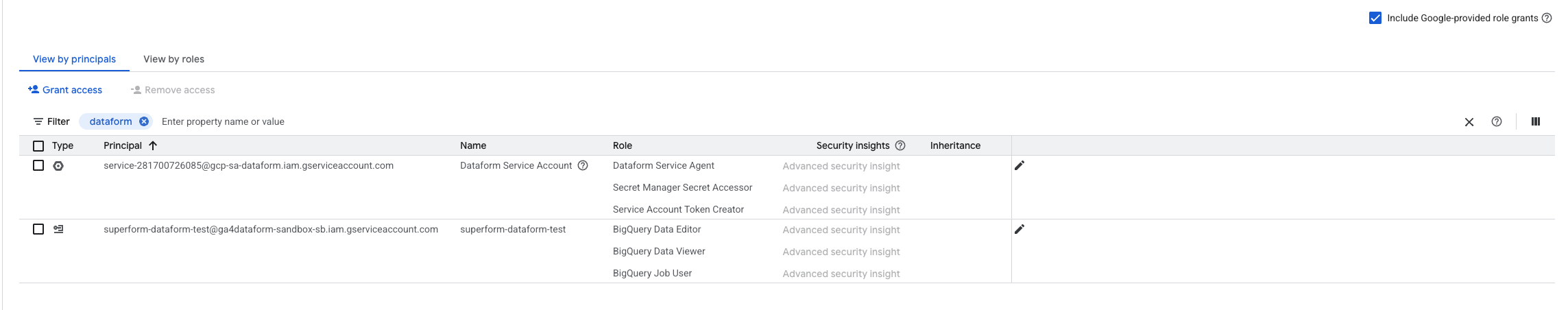
Additionally, Dataform will automatically grant the Dataform default service account access to the custom service account. The Dataform Default Service account will be listed as "Principals with access" of Custom Service Account. This action is performed automatically by Dataform when configuring the workflow by selecting the Custom Service Account as the service account executing the workflow.